
There has been startling news from USA and UK intelligence agencies stating that VPN products have a flaw that hackers are exploiting. The news is particularly worrying as Virtual Private Networks aim to stop hackers from gaining access to data. Perhaps more worrying is the fact that not only do they have a flaw… multiple vulnerabilities have been found.
What are the vulnerabilities?
The US National Security Agency and the National Cyber Security Centre in the UK both warned that VPN products are vulnerable. However, where do the vulnerabilities lie?
Apparently, the two intelligence agencies have warned about persistent threat actors who are exploiting VPN vulnerabilities known to affect products.
This is not the first time that VPN products have come under fire. In 2018, three popular providers were warned they had suffered IP leaks of data that might be sensitive. Providers mentioned included Palo Alto, Fortinet and Pulse Secure.
Multiple VPN application vulnerabilities
The NSA has raised awareness of multiple vulnerabilities affecting Virtual Private Network applications.
The intelligence agency warned that a hacker could take advantage of the vulnerabilities and take over an affected system. At the same time, the NCSC said they are also looking into exploitation of three flaws in VPN products.
The CGHQ agency revealed that activity is ongoing. The activity is targeting international and UK organisations, including the military, government, healthcare and business sectors.
The vulnerabilities lie in several SSL VPN products allowing hackers to get hold of files. These contain authentication information. Essentially, hackers use them to connect to the VPN and change the configuration settings of the network.
With access to the VPN hackers can run secondary exploits, which could allow them to access a root shell.
According to agencies the vulnerabilities are documented in open source. Meanwhile, data suggests many hundreds of UK hosts face vulnerability.
Security experts advise organisations patch
Security experts have advised organisations using a VPN to patch as soon as possible to avoid the vulnerabilities. However, the vulnerabilities are downloadable now so fast action is needed.
The vulnerabilities have been used recently, despite the fact they have been known about since August. Organisations should review logs and check for abnormal activities on devices. Security experts warned organisations they should also reset authentication on any device that may have been exploited and use multi-factor authentication.
VPNs provide protection
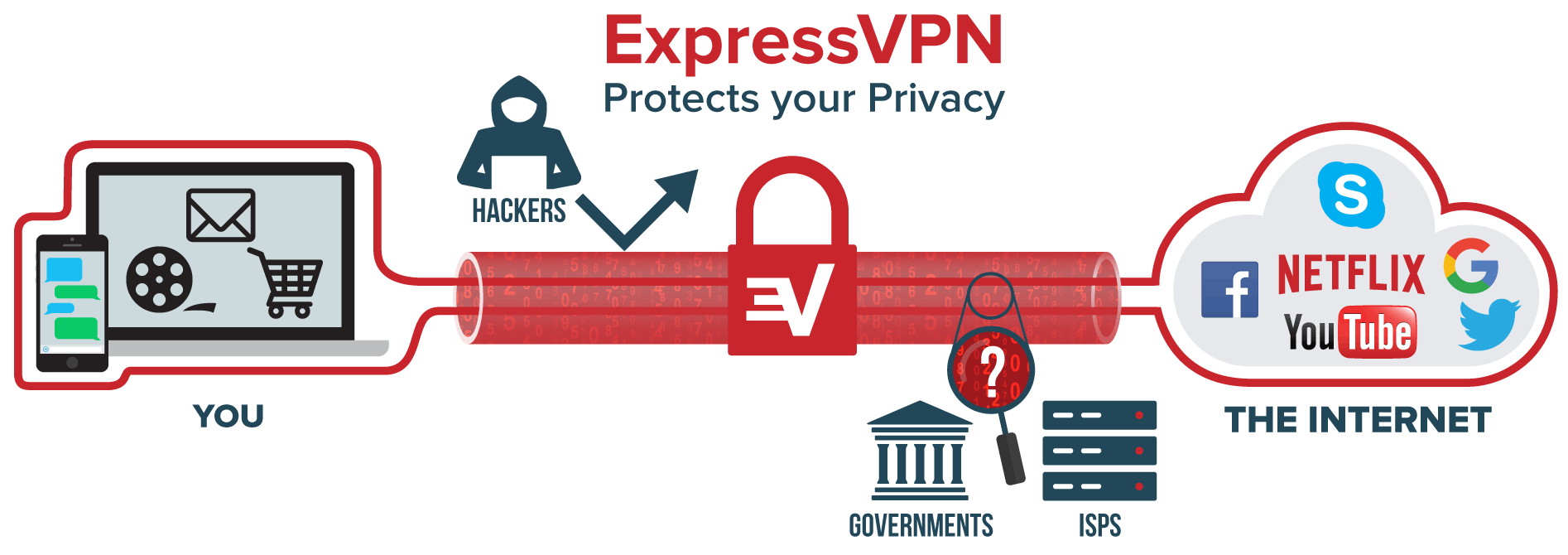
One of the many uses of a VPN is to offer protection via a secure encrypted tunnel. This allows users to browse the internet knowing hackers cannot read any information sent from the protected device onto the internet. Another use is to overcome geo-restrictions and censorship.
Are VPNs still useful?
VPN protection is still extremely useful. Moreso, it is important to remember that the vulnerabilities do not apply to all providers.
Therefore, it is essential to choose wisely. Care should be taken when choosing a provider. Choose the best trustworthy and reliable VPNs out there to increase security when using a Virtual Private Network.
In our case, we highly recommend ExpressVPN, NordVPN and CyberGhost. These are three top providers who take security and safety of users extremely seriously.
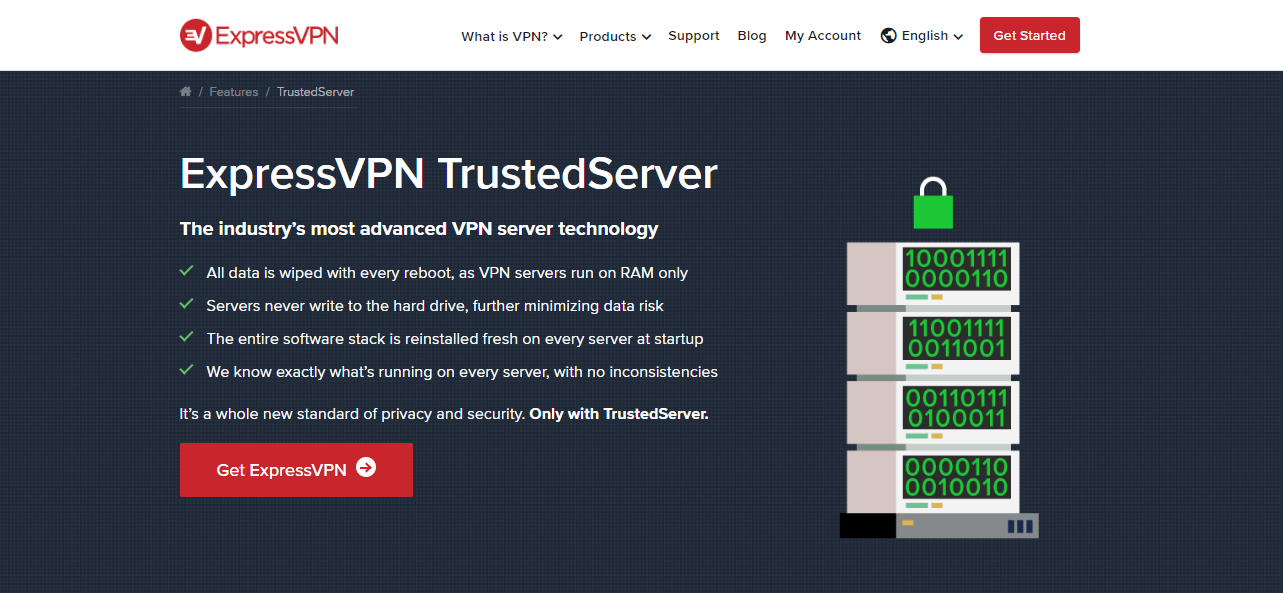
All three providers offer advanced security features to provide protection when browsing. Encryption is by way of AES-256-bit and security experts around the world rely on it.
In simple terms, it means that a brute-force attack would be infeasible.
All three providers offer a range of security protocols. Users can use the recommended protocol, however, they can also swap to one of their choice. In the case of ExpressVPN, protocols include UDP – OpenVPN, TCP – OpenVPN, L2TP – IPsec or PPTP.
The providers all have strict no logging policies and we already told you how important it is to choose a VPN that does not keep logs. If the provider does not keep logs, there is nothing for hackers or anyone else to discover about you.
Avoid vulnerabilities with ExpressVPN now >
Vulnerabilities exist with VPN products. However, you may be far more vulnerable if you risk using the internet without one on place.

A professional writer with a Master’s degree in Mechanical Engineering. Since his youngest age, he loves everything related to internet, technology, fitness, games, and dogs! He joined our team in order to bring his deep knowledge in security services, among which VPN is of course a key component.





